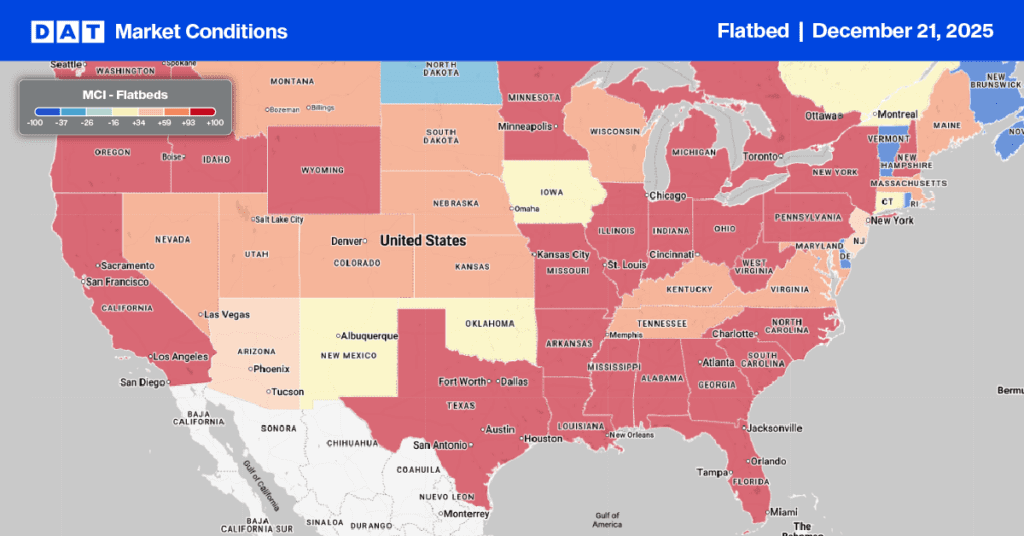
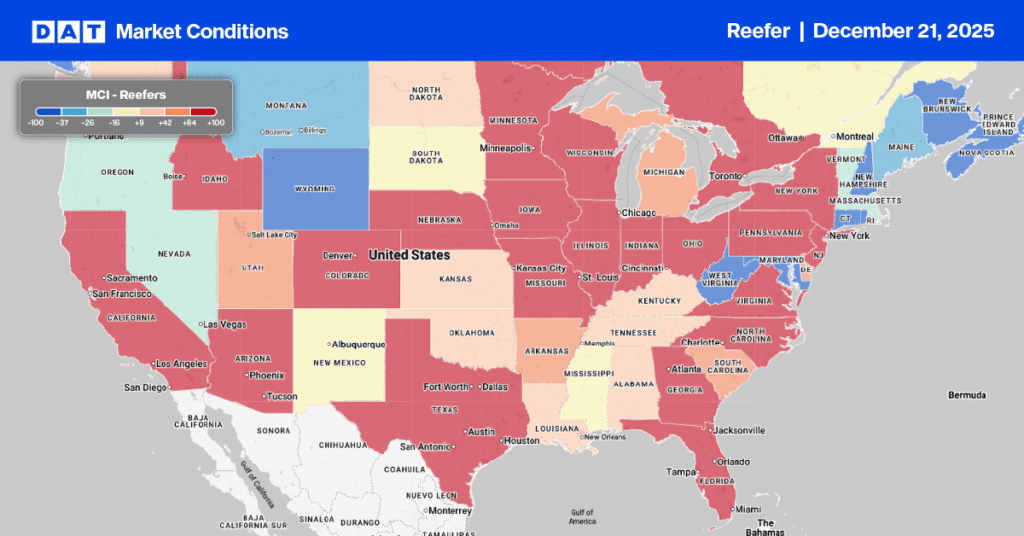
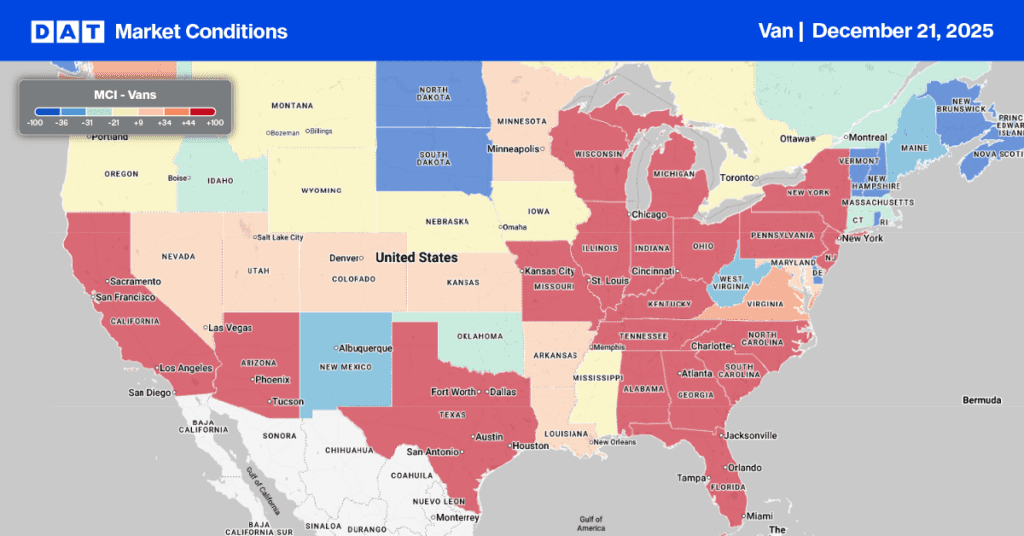
Fighting fraud in trucking is a team sport, and according to Erika Voss, Chief Information Security Officer at DAT Freight & Analytics, slowing down is key. It’s easy to get caught up in the rush to book a load, but for carriers, the best advice is to take a moment to look more closely at the email or text in question.
On a recent DAT Freight & Analytics show, we discussed the latest trends in cybersecurity and fraud; here’s a summary:
Dean Croke:
What are some of the latest trends in trucking cybersecurity?
Erika Voss:
The latest trend is “vishing” which involves being attacked through your text messaging. On top of that, Colorado State University recently published that ELDs are starting to be a way to be a new attack vector. The ELD is an electronic device providing another way for a hacker to get in and take control of your network, steal data, or just disrupt the entire fleet as is the case in many ransomware attacks. It’s just a different version of a ransomware attack in the trucking vertical.
Chad Kennedy:
Are there some top tips that you can give on how to prevent attacks and how to respond to them if you do? And how do you notice that you’re getting attacked?
Erika Voss:
To notice you are getting or have been attacked is really going to come from having some type of intelligence, some type of threat intelligence. I know that’s hard for small carriers, or small, you know, entities you know that only have like you said, five or 10 trucks. I tell people to go out and look at the resources that are available to them. They’re free. Also, it will tell you some tips and tricks that you can think about specifically for your business. The big thing I do tell people is you’ve got to report the suspicious activity. I know it’s hard. I know a lot of people don’t want to file against their insurance.
Dean Croke:
Is cybersecurity in trucking becoming a new role we all should be thinking about?
Erika Voss:
I think that’s the missing piece. You need to have somebody dedicated to your actual security. You can no longer be successful if you have cybersecurity as part of your technology — you can’t just get away with just having a technology leader anymore. You need to have somebody who’s looking at your cybersecurity as well.
Dean Croke:
We often hear someone has been hacked, but that’s not always the right term. How should we think about terminology?
Erika Voss:
Often when someone says, “I’ve been hacked”, what they’re really saying is your account has been compromised, they haven’t been hacked at all. It’s an account that’s been compromised because of poor cyber hygiene and/or passwords and other account credentials have been shared with more than one person. If you don’t address even those basic cyber hygiene things, you’re going to continue to be attacked.
Chad Kennedy:
What’s some advice you can give to shippers, carriers and brokers?
Erika Voss
Use multi-factor authentication and don’t click the link. That’s the worst thing you could click. You want to be prompted all the time to resubmit your credentials because you’re controlling your identity. The bad guys are coming at you through some type of device that you’re holding. And so if I can get you through a phone, or if I can get you through a text message, and if I can exploit you and you want to share your credentials with me, I mean, that social engineering attack is literally going to cause havoc for you.
Chad Kennedy:
What do you anticipate changing over the next 12 months in cybersecurity in our supply chain?
Erika Voss
I think you’ll start to see that people need to invest in hiring some type of head of security or a CISO. I think you’re going to see organizations realize their attack landscape is very different. They will have to go deeper, and there’s their supply chain. Companies will have to look at their third-party vendors and ask who that vendor outsources to. We’re great at looking at that tier one, but you need to go deeper. Companies will need to look at tier two, tier three, and tier four.
The complete interview can be found here.